After the Veeam Decoy Project a few months ago, here is another very interesting tool developed for the Veeam community.
This is once again an open source project in the security area: integrated with Veeam Backup & Replication, it enables vulnerability assessments on existing backup data, using the open source tools Trivy and Grype.
The solution is designed to help manage situations such as security incidents, during which a specific server may be required to be restored at a specific point in time. Using vScan, it is possible to analyze that backup and check what vulnerabilities it has at the OS level (Linux only) before putting it back into production.
What would happen, in fact, if an attacker was still in our network ready to exploit our systems again?
Let’s explore some details of this tool.
Installation requirements
- OS (client): Windows 10+
- CPU: 1 core
- RAM: 512 MB
- Disk: 500 MB
- Software: VBR console e Veeam Powershell module
- Veeam version: 12.x
- Linux server for scan: Rocky Linux 9.x / Ubuntu 22.x
- Backup support: vSphere VM, Linux OS
- Credentials Linux Server for Scan: root or user with sudo
- Ports: 9392, 22, 587
- Internet Access
You can download the software from the following address: https://github.com/VeeamHub/veeam-vscan-security
Method of use
- Open the application with administrative rights
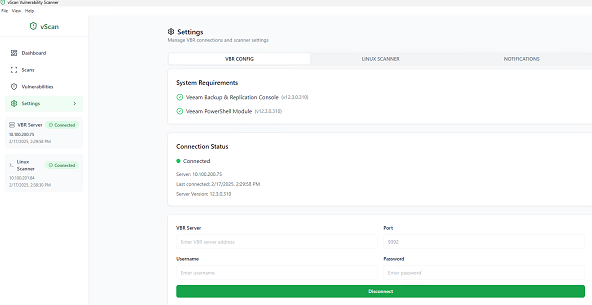
- Under settings, validate the presence of the VBR console and Powershell module
- Enter the credentials of the VBR
- Select a linux scanner from the list of servers in the VBR or specify an external one
- Test and save the configuration
- Configure settings for email notifications (optional)
- Select server, disk and restore point of which to scan (multiple selections can be made by adding scan “queue”)
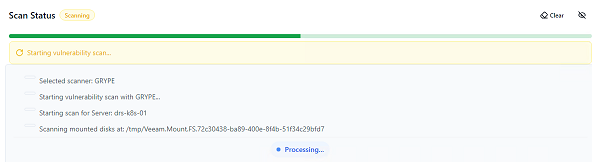
- Perform the backup mount operation and select an engine for the scan
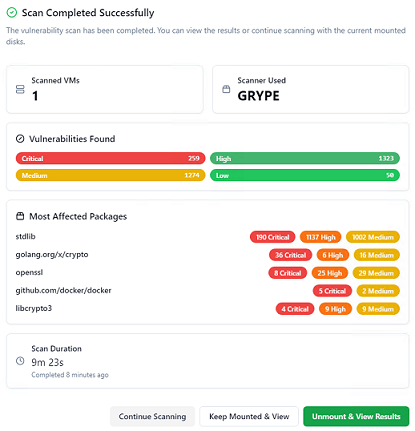
- Analyze or export the generated results
Features Summary
- Integration with Veeam Data Integration API
- Integration with Security Scanner Trivy and Grype
- Automatic installation and update of definitions
- Granular selection of backups
- Use of a managed or external VBR linux server for scanning
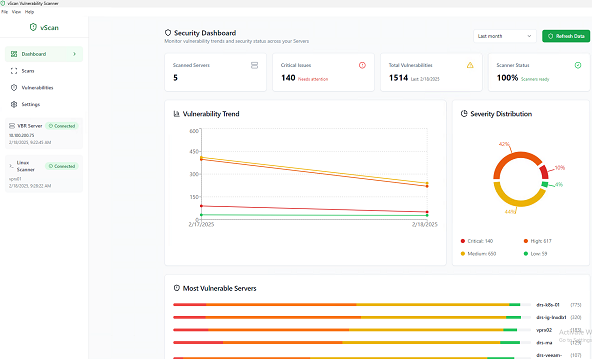
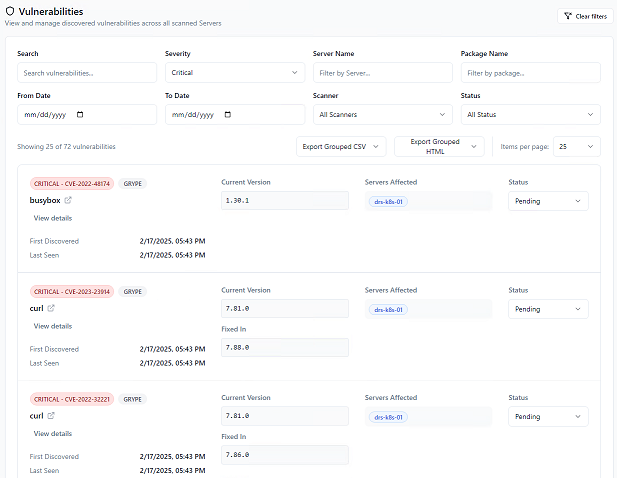
- Dashboard with vulnerability and severity trends
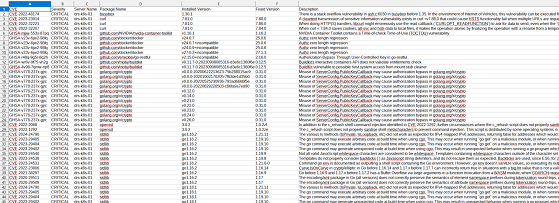
- Vulnerability list synchronized with Nist NVD and Github Advisory database
- CVE check contained in the CISA Known Exploited Vulnerabilities catalog
- Status tracking of detected vulnerabilities
- Ability to filter detected vulnerabilities by severity, status, server name, etc.
- Export of results to CVS/HTML
- Email notifications
- Connection status
Conclusion
The tool is very simple to setup and use, the graphics is minimal but attractive. This version only supports scanning Linux machines on VMware, but there will be improvements for sure in the next releases.
Obviously, it is not to be considered as something to prevent security incidents or to be used as a replacement for the more classic vulnerability assessment tools on live production systems.
Instead, it can be categorized, alongside the malware detection features already included in the latest versions of Veeam such as Antivirus/YARA Scan and Veeam Threat Hunter, as an extra weapon to perform additional checks on our last barrier of defense, the backup data.
Enjoy! 💚