In a previous post, we went to explore the new and more interesting features of Veeam B&R version 12.1.
In this post we will go into more detail about the tool that allows us to keep an eye on the status of our backup infrastructure: the Security and Compliance Analyzer.
INTRODUCTION
When we design and implement our backup infrastructures, paying attention to security rules is now a must.
There are a number of general considerations that help us harden our servers, as well as many best practices that should be applied to our backups.
The new Security and Compliance Analyzer tool allows us to have just such a simple and intuitive overview of the implementation of these best practices on our backup server.
Let’s go through its functionality in detail.
THE TOOL
Access to the tool is clearly visible in the main bar of the Veeam Console:
As anticipated earlier, the checks are divided into two sections, “Backup Infrastructure Security” and “Product Configuration“.
BACKUP INFRASTRUCTURE SECURITY
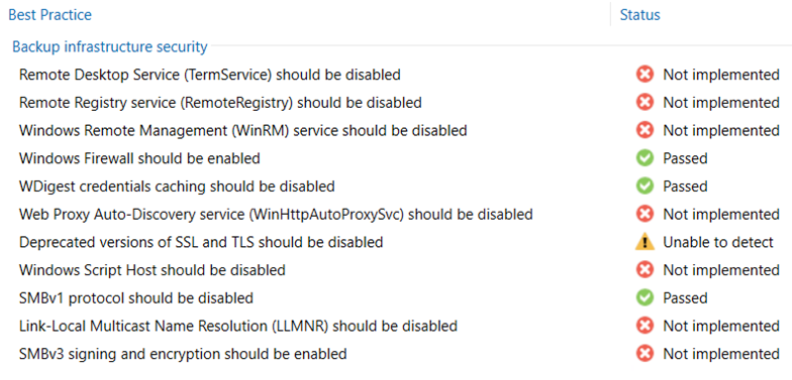
As we can see, it is concerned with checking the implementation of certain best practices defined for the Windows operating system hosting our backup server.
- The first settings that are recommended are to disable those services that are considered critical because they allow remote interaction with our server, which are “Remote Desktop,” “Remote Registry” and “Windows Remote Management“.
- Then we move on to the rarely considered Windows Firewall: the best practice is to keep it active always, going to work with the inbound and outbound rules as needed. Note: Veeam B&R automatically creates the firewall rules necessary for its components to communicate with each other.
- It is then recommended to disable the “WDigest credentials caching” and “Web Proxy Auto-Discovery service” features to prevent credential or MITM-type attacks.
- The next check is on deprecated versions of SSL and TLS, such as SSL 2.0, SSL 3.0, TLS 1.0 and TLS 1.1, which should also be disabled.
- As for potential script-based malware attacks, good practice is trying to limit them by disabling the “Windows Script Host“.
- Returning to deprecated protocols, SMBv1 is also among those to be disabled, as it is affected by numerous vulnerabilities. Note: As of Windows Server 2016, it is disabled by default.
- The last protocol to be disabled is the “Link-Local Multicast Name Resolution” to limit spoofing and MITM attacks.
- Finally, security on the SMBv3 protocol is tested, checking that settings to prevent NTLMv2 relay type attacks are enabled.
PRODUCT CONFIGURATION
We now move on to controls on the software-side settings.
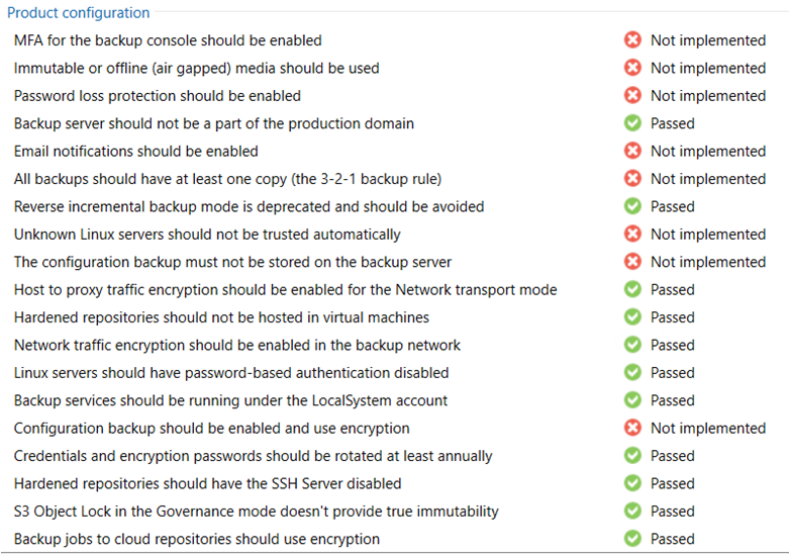
The strategies and configurations that Veeam recommends are obviously focused on preserving our backups.
- MFA for the VBR console: since v12, multi-factor authentication can be enabled on the backup console.
- Immutable or offline media: to protect backup files, we recommend using at least one repository with the data immutability feature enabled or media that can be disconnected from the network, such as tape or rotated drives.
- Password loss protection: a setting in Veeam Enterprise Manager that allows us to decrypt our backup data in case the encryption password is lost.
- Domain or non-domain?: Veeam recommends that we leave our server, and the other infrastructure components, at Workgroup. Note: In case we want to use join with AD, it is good practice to create a management domain dedicated exclusively to the backup environment.
- Email notification: always remember to enable email notifications, it is essential to keep track of the outcome of backups and other events happening in the system.
- 3-2-1 rule: the golden rule advises us to have at least 3 copies of the data (including the original data, so two backup copies), on at least 2 different media and 1 offsite copy. Note: The rule has now evolved into 3-2-1-1-0, where the second 1 is the offline/immutable copy, and the 0 indicates the need to implement an automated validation procedure for our backups, and error-free during verification testing.
- Reverse Incremental: is the method that produces more read and write operations on our repository, to be abandoned in favour of the standard incremental.
- Unknown Linux servers: in case we need to add linux servers to our backup infrastructure, it is recommended to trust them manually rather than automatically.
- Configuration Backup: as a best practice, the configuration backup should be saved to a repository external to the backup server itself. Note: from v12.1 you can select an immutable object storage repository for this task as well.
- Proxy traffic encryption: if our virtual proxies use network transport mode, encryption (NBDSSL) is recommended.
- Physical Hardened repository: to reduce the attack surface, the hardened type repository should reside on a physical server (and with local disks) instead of a virtual one.
- Network traffic encryption: to enable secure communication in our backup network, both to the Internet and to private networks, it is recommended to globally enable encryption in the general software settings.
- Linux authentication: best practice recommends that we do not use password-based authentication for our linux servers, but enter SSH through the use of the public-private key pair, preventing brute force and MITM type attacks.
- Backup services: it is recommended to use “Local System” as the account for our Veeam services.
- Configuration backup encryption: it is recommended to use encryption on Veeam’s configuration backup as well, for more secure management of sensitive data in the DB.
- Password rotation: control is over the credentials of the various components added to our backup infrastructure and the encryption password, which should be changed at least once a year.
- Hardened repository access: as a best practice, SSH on this type of repository should be disabled.
- S3 object lock type: this check verifies that the immutability set on the S3s added on Veeam is Compliance type (not editable) and not Governance type (editable), going against any policies on data handling (e.g., GDPR) and of course the security of effective immutability of backups.
- Backup encryption: especially if our backups are saved to a cloud repository, it is a good idea to enable encryption at the individual job level.
- Latest updates: it is recommended to keep the Veeam B&R software updated to the latest release/patch.
IMPLEMENTATION
To facilitate the implementation of most of these best practices, Veeam has provided on its KBs a powershell script that fixes all 11 points related to backup infrastructure and 2 points related to product infrastructure, while the settings that need custom setups (such as, for example, setting up our mail server, choosing a repository, users for which to enable MFA, etc.) are obviously in the hands of the backup administrator to be configured manually.
Below is the link to download the script: https://www.veeam.com/kb4525
USE
The tool can be used both interactively and automatically.
It is possible, in fact, to set up a report with daily scheduling and emailing.
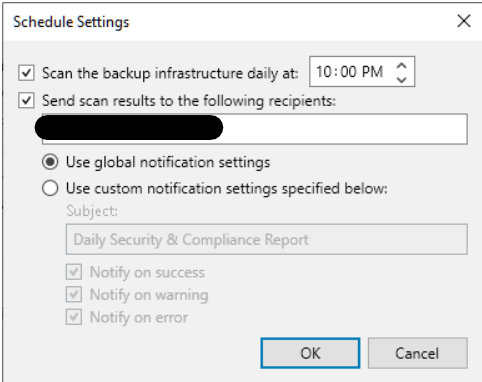
Finally, it is also possible to exclude one or more parameters from the controls by marking them as “suppressed“.
CONCLUSION
We will never tire of repeating how important security is, especially for backups, which are our last defense against loss or corruption of our data. This improved tool is a good starting point to help us keep things under control.
We conclude the post by reposting other useful links regarding security and best practices, with the hope that the Security and Compliance Analyzer will also be increasingly developed and improved according to the evolving guidelines.
https://helpcenter.veeam.com/docs/backup/vsphere/security_guidelines.html?ver=120
https://go.veeam.com/rs/870-LBG-312/images/veeam-security-checklist.pdf
https://go.veeam.com/rs/870-LBG-312/images/veeam-security-best-practices-2022.pdf
Enjoy! 💚