INTRODUCTION
The topic of security is on the daily agenda for us professionals in the IT world nowadays: news of hacker attacks, data breaches, and ransomware requests are no longer news, but are unfortunately everyday occurrences.
💡: for staying up-to-date on the latest ransomware attacks around the world and many other insights on the topic I suggest checking out the Ransomware Live site
In this scenario, Veeam Data Platform 12.3 helps us protect our data and reduce the impacts of a cyberattack.
Let’s find out what are all the security-oriented features built into the software.
SECURITY FEATURES
The latest Veeam 12.3 release brings with it many security features that have been gradually introduced and improved over the years by the leading US Data Protection company.
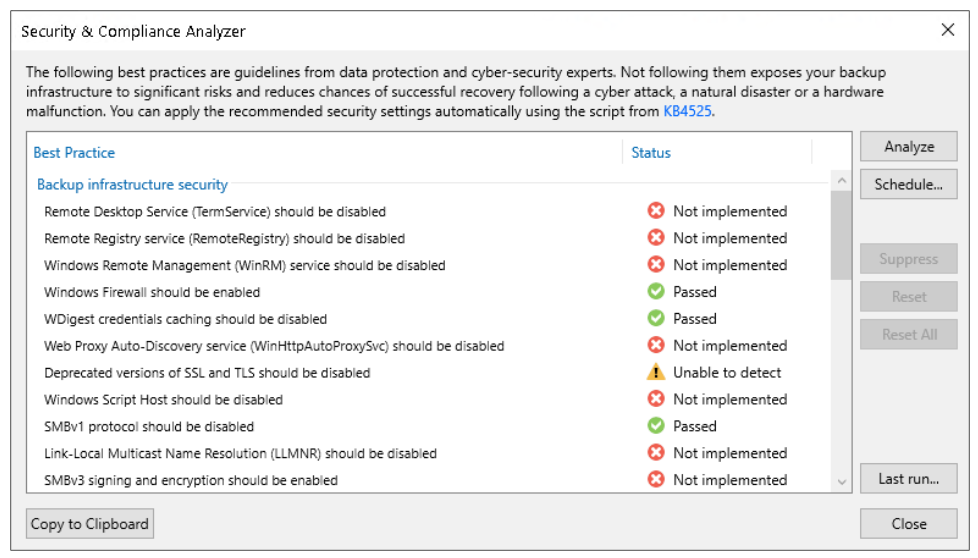
Security and Compliance Analyzer
It is a tool integrated into the VBR console, it analyzes several configurations of backup infrastructure components by checking compliance with suggested security best practices.
Some examples: disabling obsolete/vulnerable protocols, verifying presence of hardened/immutable repositories, 3-2-1 rule, encryption password complexity, having the latest patches installed
💡: you can schedule the automatic scan and send it via email
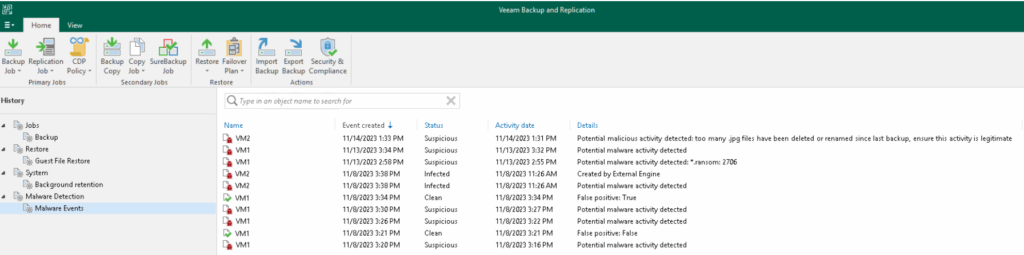
Malware detection
It is the real engine of cybersecurity built into Veeam 12.3, and includes several features. Below are the details:
1) guest index data scan
Supported for VMWare, Hyper-V, Nutanix, and Veeam Agent for Windows backups, allows you to scan the indexes of a file system (upon enabling the “guest file system indexing” option on the backup job) and flag any suspicious files/extensions with a specific event in the VBR console.
It is managed by the Veeam Data Analyzer Service, which at the end of each backup compares the indexing contents with the “SuspiciousFiles.xml” file, where indeed a (customizable) list of suspicious files and extensions is contained.
💡: for backup servers that have internet browsing blocked to Veeam addresses as well, you can manually update the list of suspicious files by downloading the “SuspiciousFiles.xml” file following this KB
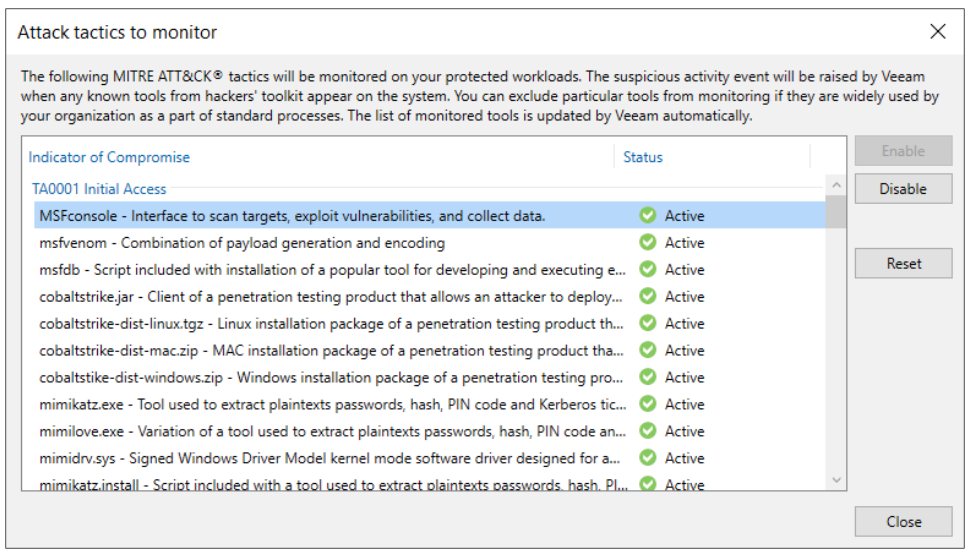
This xml file also contains a list of the IoCs (Indicators of Compromise) selected from the matrix developed by the MITRE ATT&CK, i.e., files that are not malicious but may indicate the presence of suspicious activity in progress. In this case, the Veeam Data Analyzer Service compares the indexing file of the last two restore points (created at least 25 hours and maximum 30 days apart), looking for any potential indicators of compromise. It is also possible here to choose which default IoCs to monitor and which not.
Another feature also managed by the Veeam Data Analyzer Service is the one that identifies any multiple file deletions: by comparing the indexing file of the last two restore points (created within a time window of at least 25 hours and maximum 30 days), if there are at least 100 files of a specific extension and in the last restore point more than 50 percent of the total are deleted, a malware detection event is created. Extensions are recorded in the file “TrackedFiles.xml”, which can be customized by changing the parameters of Thresholdpercent and Thresholdfiles, or even adding specific extensions or ignoring file system paths that we do not intend to monitor.
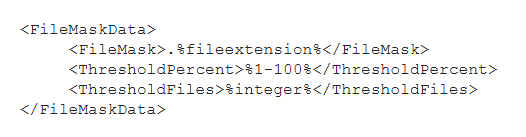
Finally, with the same logic of comparing the indexes of two restore points, the presence of multiple extension changes is also identified; based on the occurrence of certain conditions, this time not customizable, such as at least 200 files with new extension and not present in the “SuspiciousFiles.xml”, a malware detection event is triggered.
💡: logs of malware detection events, in addition to the dedicated section within the VBR console, can be accessed in the default path “C:\ProgramData\Veeam\Backup\Malware_Detection_Logs”
💡: you must also consider that by default the indexing data is kept in the Veeam Catalog for 14 days. If you want to increase this value, you can use the Veeam Enterprise Manager, which will maintain an extra copy of the Catalog with configurable duration
2) inline scan
While the features just described are based on post-backup analysis at the file system level, inline scan acts at the image/block level during a backup, detecting possible entropy generated by malware, such as encrypted files or artifacts, text files that may contain onion links or ransomware notes.
Technically, during each backup session on the Veeam Proxy used, files are generated (RIDX format, one file for each virtual disk processed) containing the disk metadata (disk name, creation time, disk size, used size, sector size, partition table) and ransomware data (encrypted data, file types, onion addresses, ransomware notes). After the backup is complete, these files are copied to the VBR Catalog, and scanned by the usual Veeam Data Analyzer Service, which will then save the results of its analysis in the “RansomwareIndexAnalyzeState.xml” file. When a new restore point appears, the service compares the most recent and oldest RIDX file (created in a time window of 25 hours and maximum 30 days), going on to update the “RansomwareIndexAnalyzeState.xml” file. If anything suspicious is identified, a malware detection event is created and the object, the specific virtual machine, marked as “suspicious”.
💡: the inline scan feature is disabled by default; in case you want to enable it, keep in mind that it increases the CPU usage of the proxies and RAM/Disk space of the VBR
💡: to check in detail which files have been identified as “encrypted data,” use the procedure provided in this KB
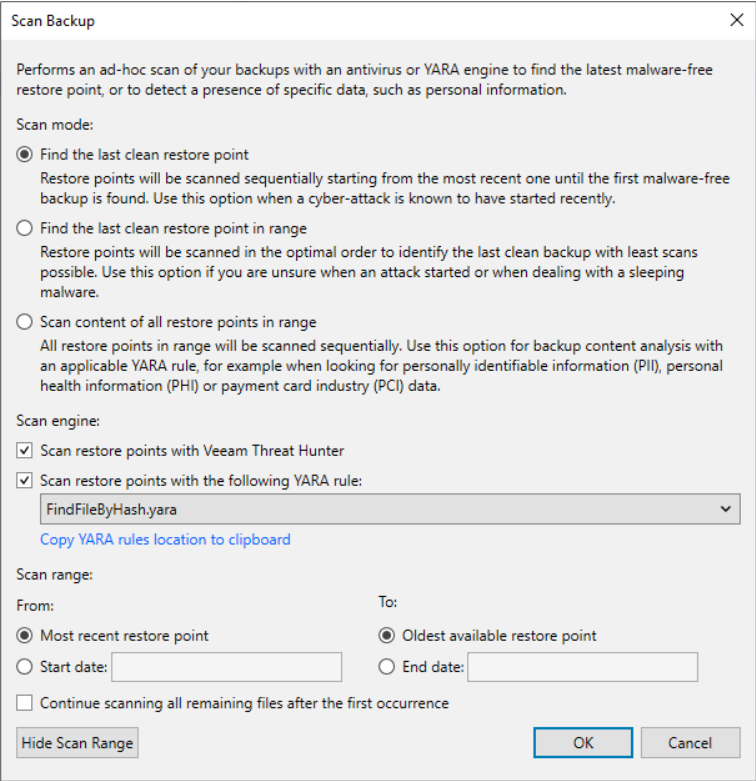
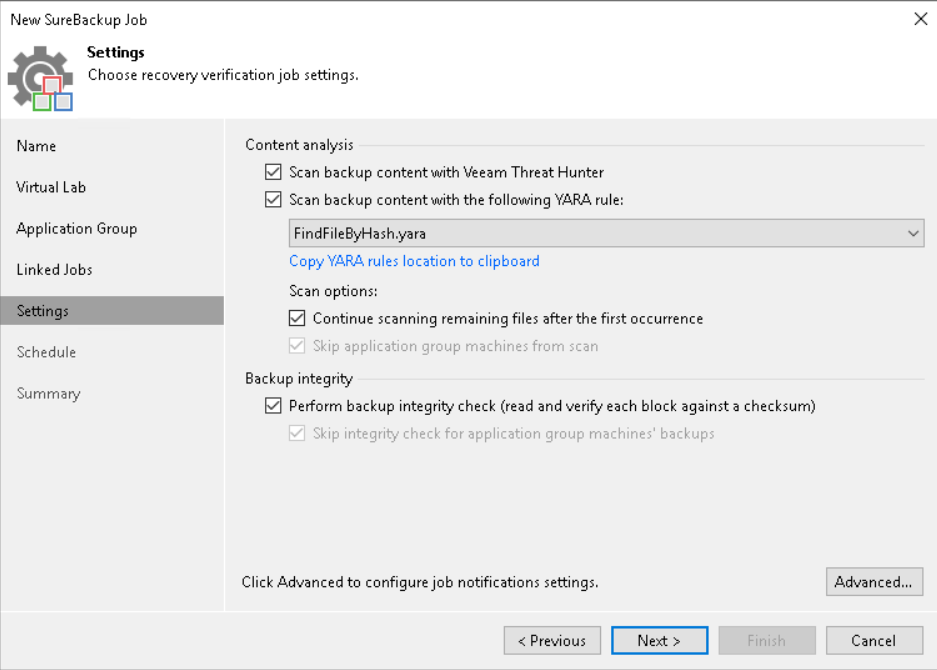
3) scan backup – signature detection
Using this feature it is possible to find a clean restore point (not infected with malware) or to identify specific information, such as sensitive data. Currently, scanning only Windows servers (VMs or agents) via, precisely, a Veeam mount Windows server is supported.
There are three engines that can be used for scanning:
- veeam threat hunter, a Veeam service automatically installed on mount servers and running in the background. Before each scan, it is checked for any malware signature updates. 💡: a registry key can be set to configure file and folder exclusions from the scan
- 3rd party av, as an alternative to the veeam threat hunter, you can use a third party antivirus pre-installed on the mount server; you can find information about the default avs and add custom ones using the “AntivirusInfos.xml” file in the mount server.
- yara rule: using files with a well-defined syntax, it is possible to search for infected restore points or sensitive data. In the former case, if a clean restore point is not found, a malware detection event is generated.
Whenever the scan finds a restore point that is not clean, it is marked as “infected”. If the scan session finds at least one clean restore point, it ends in “success,” otherwise in “failed.”
💡: it is possible to suppress the event generation by inserting this line within the yara file: <rule SearchFileHash : SuppressMalwareDetectionNotification>
💡: the complete scan logs can be found in the following directory of the mount server C:\ProgramData\Veeam\Backup\FLRSessions\Windows\FLR__<machinename>_\Antivirus
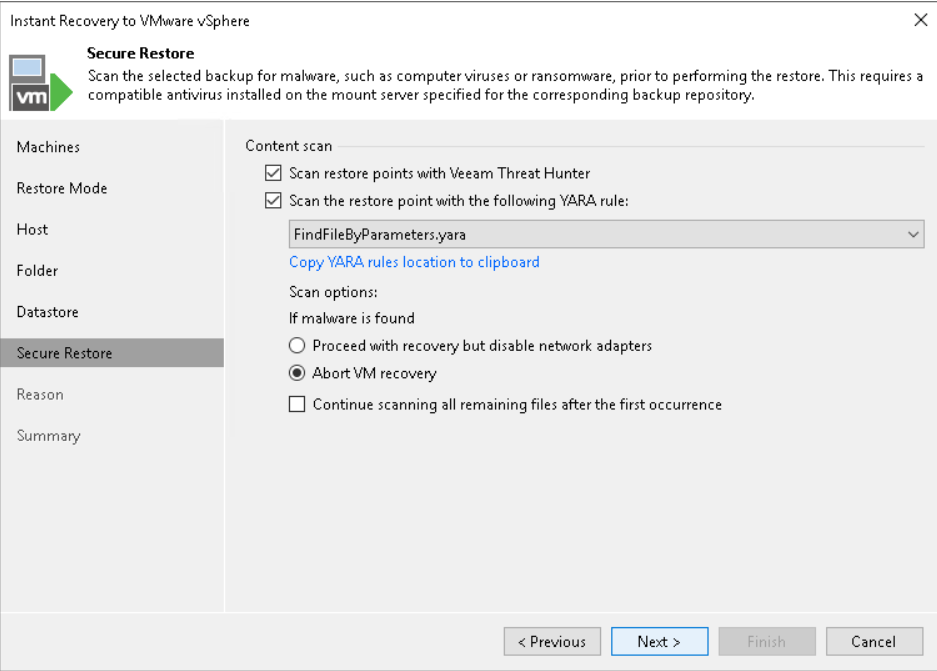
Secure restore
This feature allows the scan engines described above to be exploited during a restore.
Specifically, the following scenarios are supported:
◦ Instant Recovery
◦ Virtual Disks Restore
◦ Entire VM Restore
◦ Restore to Microsoft Azure
◦ Restore to Amazon EC2
◦ Restore to Google Compute Engine
◦ Disk Export
💡: you can schedule automatic scanning of backups using SureBackup
💡: if you have VRO, you can take full advantage of automation features in a clean room environment
Incident API
Veeam not only leverages its own malware detection capabilities, but also offers the ability to integrate third-party tools.
By exposing Veeam’s specific REST API, external monitoring and analysis tools are able to automate incident management and incident response processes to the point of involving the backup infrastructure as well.
In fact, an automatic quick backup can be launched upon receipt of an external threat detection event.

Syslog integration
Within Veeam it is possible to configure the forwarding of events to external syslogs, following the RFC 5424 standard
It is possible to exclude the forwarding of certain events, either by entering them manually in the interface or via xml files.
💡: the full list of events managed by Veeam 12.3 can be found here
💡: for advanced configurations please refer to this KB
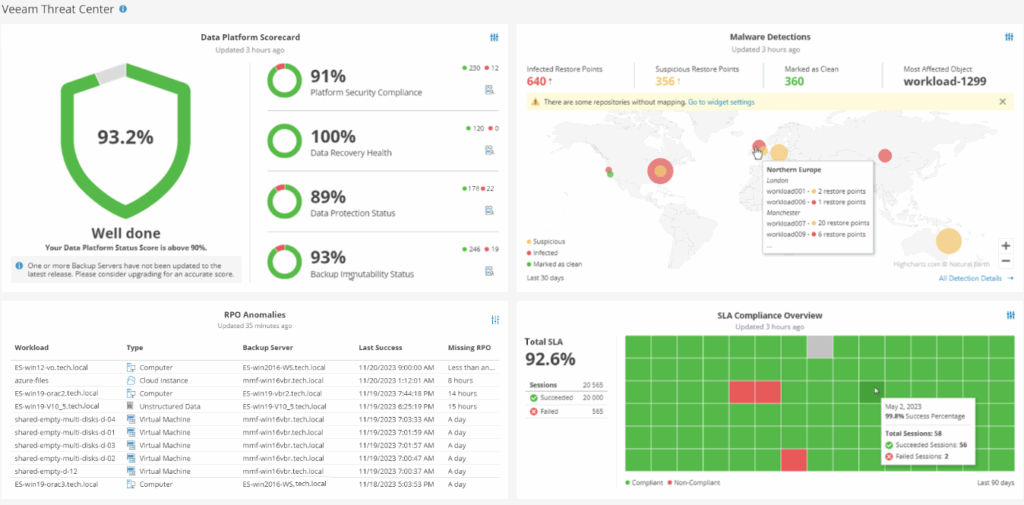
Analytics View – Veeam Threat Center
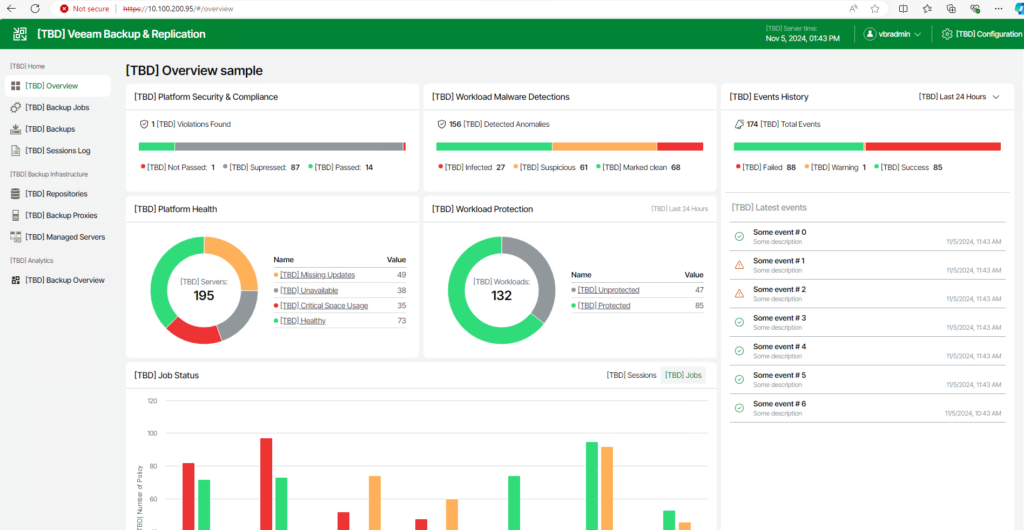
It is possible to integrate within the VBR console the view of some Veeam ONE dashboards, such as the Veeam Threat Center one, which embeds a set of information about the global security and compliance status of our backup infrastructure.
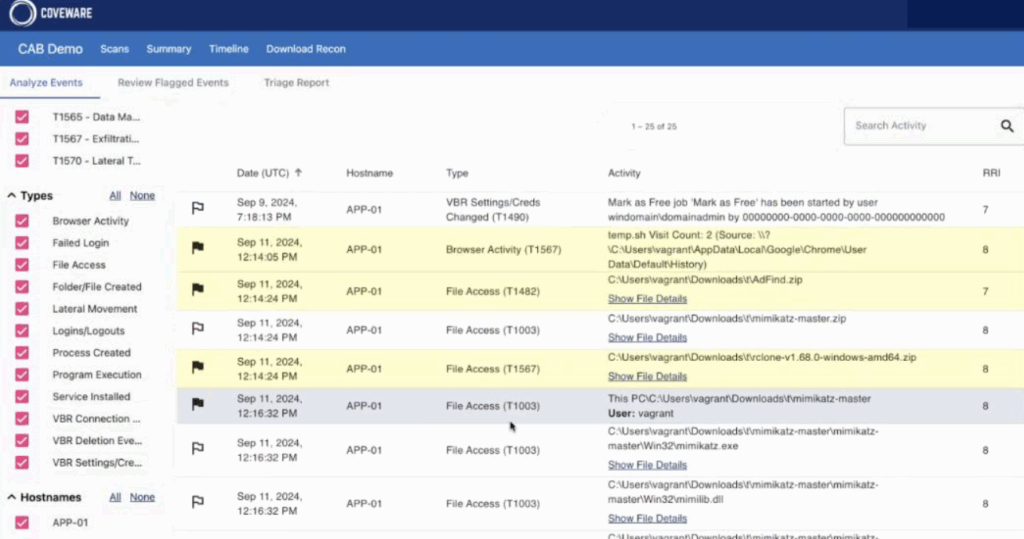
Recon scanner
This feature is one of the latest additions to the Veeam Data Platform, and is based on technology developed by Coveware, a leading Cybersecurity Incident Response company acquired by Veeam in April 2024.
It consists of installing an agent in VBR environments that continuously collects data in order to proactively identify possible suspicious activity or the use of TTPs.
With each full system scan, the agent the results can be viewed directly in the dedicated Coveware portal.
💡: it requires Veeam Data Platform Premium license version
External projects: Veeam decoy / Veeam vScan
It is also right to mention two external open source projects, but also maintained by the Veeam community. These are Veeam Decoys and Veeam vScan, which always fall under the security domain.
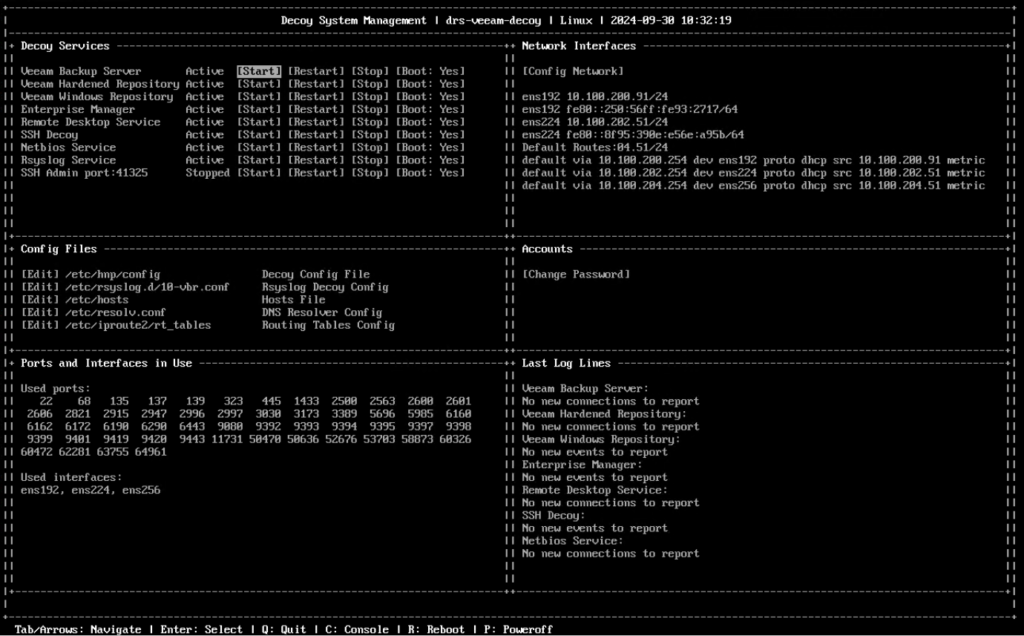
The former is a system simulates multiple Veeam and Windows services, such as Veeam Backup Server services, Veeam Hardened Repository, Veeam Windows Repository, Veeam Backup Enterprise Manager, etc. .
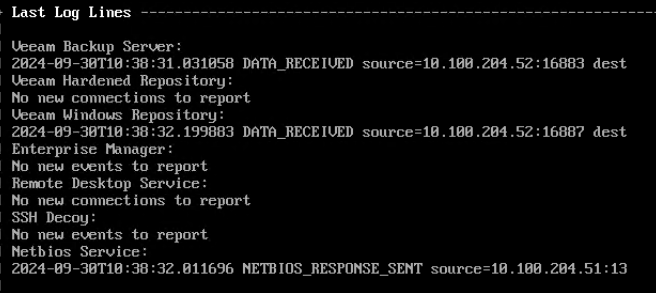
All captured connection attempts, including information such as source port, source ip, or credentials used, can be sent to a centralized syslog or via email.
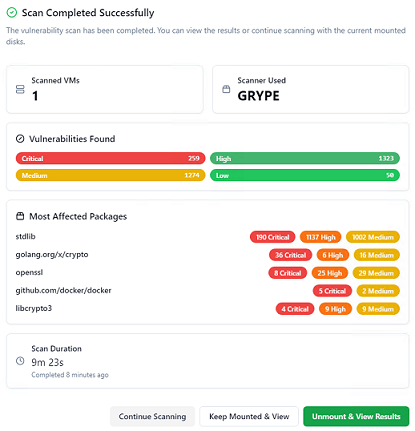
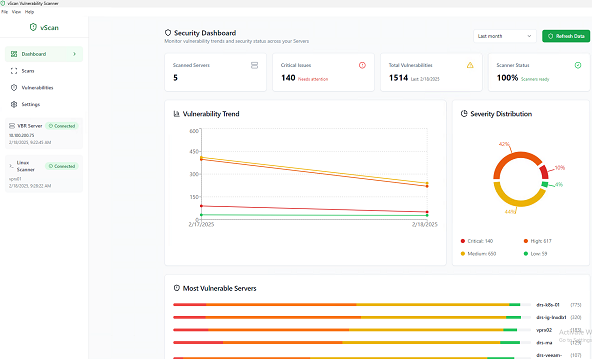
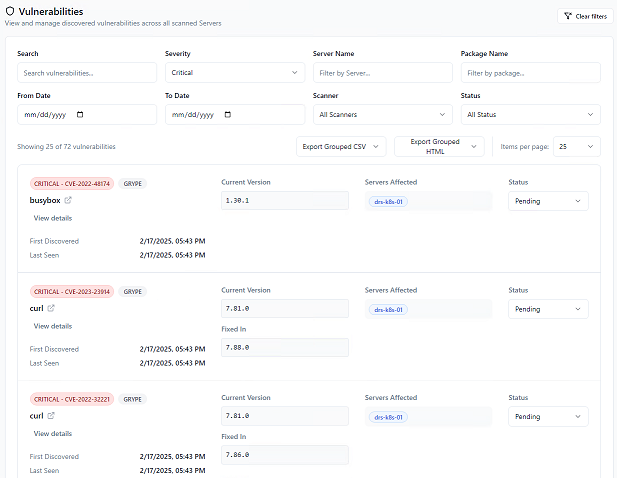
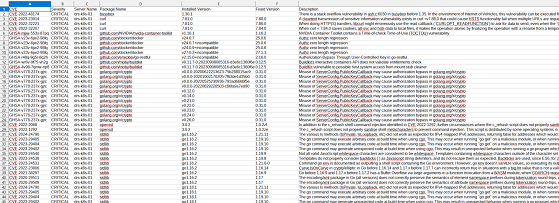
The second allows vulnerability assessments to be performed on existing backup data, using the open source tools Trivy and Grype.
CONCLUSION
In short, as we have seen the security features present in Veeam Data Platform 12.3 are numerous and useful.
We are now waiting to find out what’s new in the next versions! 💚