Let’s start from the beginning: security and backup.
Today, unfortunately, ransowmare attacks are on the rise, and defending against them is an increasingly difficult challenge.
If backups used to be considered as something not really important, perhaps useful only in case of any storage damage, today they have become the last resort to keep our data safe.
For this reason, one of the main targets during a cyber attack is the backup infrastructure: if threath actors succeed in taking it down, the road to ransom payment will be straight downhill.
News of collaborations and product integrations between large data protection and security vendors are now a daily occurrence, most recently the one between Veeam and Palo Alto Network Cortex XSIAM/XSOAR.
All this brings home to us how important it is to focus on the security of all systems, including backup infrastructure.
One of the several best practices recommended by Veeam, for example, is to try to make its components as anonymous as possible.
Assigning backup servers and repositories a name that cannot be identified with their role can be a first attempt to avoid making just about everything so easy for any malicious attackers.
Another method for attempting to identify and perhaps slow down an ongoing attack is to use honeypots: traps, decoys used to attract threat actors and draw them out.
The honeypot is a component that simulates the production system, possibly with the same applications, but with data that is not real.
In the case of Veeam Data Platform, the idea might be to create a VBR server that acts as a honeypot, perhaps even equipped with working backups.
Of course, this might require a not inconsiderable effort, because we would have to use sacrifiable, non-production systems, with the only purpose of attracting malicious attackers and having our anomaly detection software detect instrusion or tampering attempts on the honeypot.
A more simple option is the one developed by the open source Veeam Decoy project.
This system simulates multiple Veeam and Windows services, such as Veeam Backup Server services, Veeam Hardened Repository, Veeam Windows Repository, Veeam Backup Enterprise Manager, SSH, RDP, Netbios.
It supports the use of multiple network cards, so each service can be associated with a specific VLAN, so it is ready for a realistic attack scenarios using lateral movement tactics (TA0008).
The system doesn’t receive any incoming traffic, so any connection attributable to the use of discovery tactics (TA0007) should represent an intrusion attempt.
This tool can be downloaded as an OVA appliance (compatible only with vSphere 8.0 or higher) or installed on a minimal Rocky Linux.
The console comes with a very simple yet comprehensive interface where we can manage the status of decoy services, associated network interfaces, and view real-time ports in use and connection logs on each specific service.
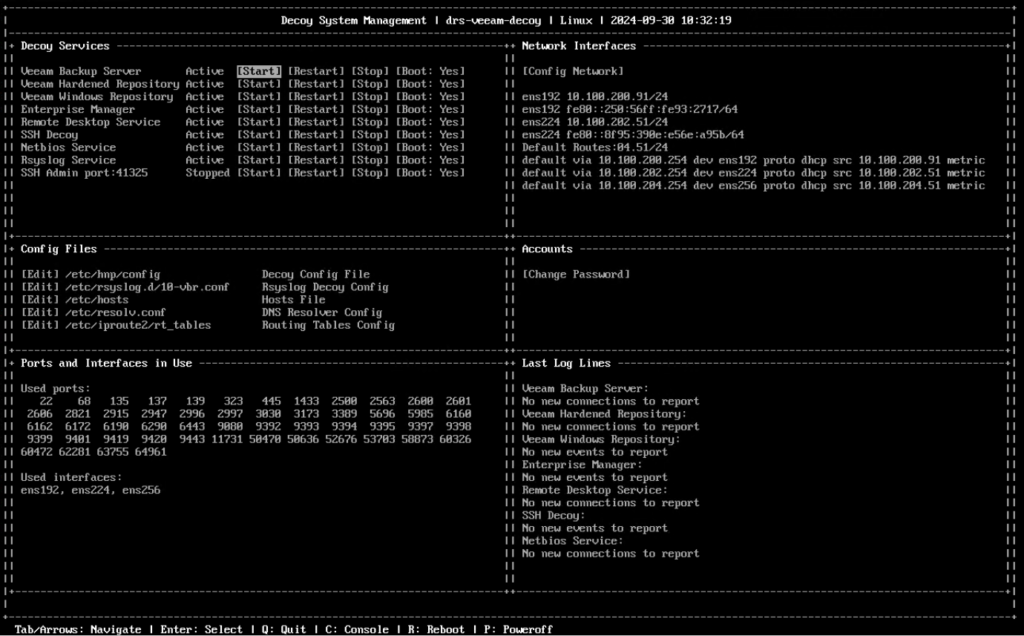
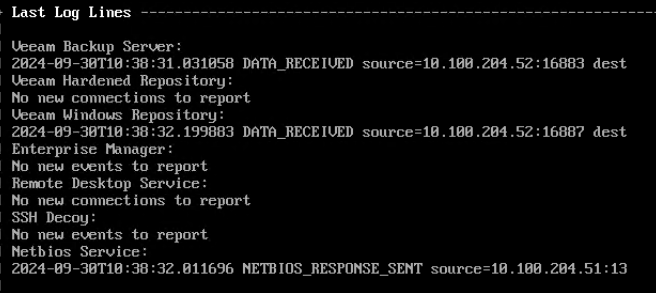
All captured connection attempts, including information such as source port, source ip, or credentials used, can be turned over to a centralized syslog or via email, so that alerting can be triggered and readily handled by a SOC.
Of course, we do not expect it to be our most effective weapon against cyber attacks, but in this battle between the two worlds it is still one more option! 💚