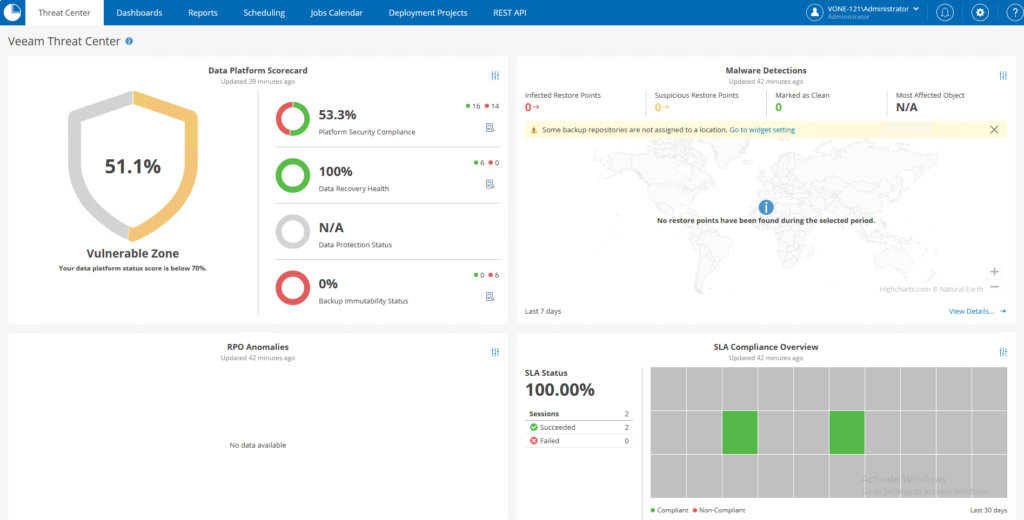
When we talk about backup repositories in Veeam, we have to mention object storage, a technology that has been growing in popularity in recent years.
From version 12 of Veeam B&R, in fact, it is possible to directly write a backup to this type of repository.
Since version 12.1, it has also been possible to back up data stored on an object storage.
Unlike file system type storage architectures, which manage data hierarchically within directories, object storage architecture is flat, and is designed to store unstructured data, such as backups.
Specifically, the data is divided into blocks with associated metadata and unique identifiers, which are used by the system when accessing it.
The main advantages include that it can hold large amounts of data at no excessive cost, is easily scalable, and is compatible with HTTP/HTTPS and REST API protocols.
Wasabi is one of the cloud-based object storage vendors, so we can compare it to the better-known S3 from AWS or Azure Blob Storage from Microsoft.
Unlike the large vendors mentioned above, the price/TB is much lower, and there are no costs for ingress/egress traffic or API calls.
Wasabi is listed in the Veeam Ready compatibility directory as an object storage backup target (S3 compatible), and with native support for immutability (object lock) functionality.
The first thing to do to use Wasabi for our Veeam backups is to create a storage account by registering for the free 30-day trial; after that, it is possible to continue using the account in Pay As You Go or Reserved Capacity Storage mode.
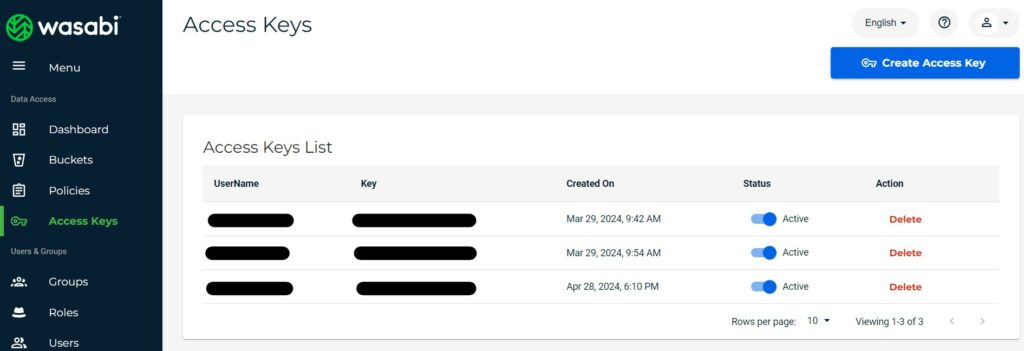
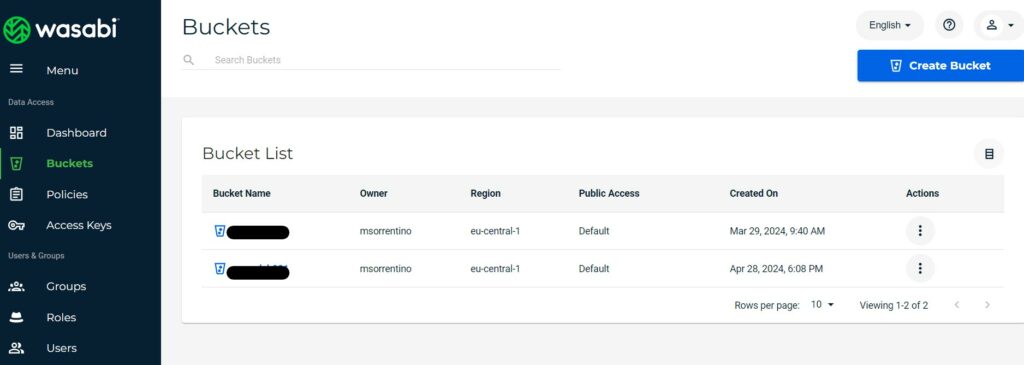
Once registered and logged into the dashboard, generate a new access key/secret key pair, and create the bucket that will store our Veeam backups:
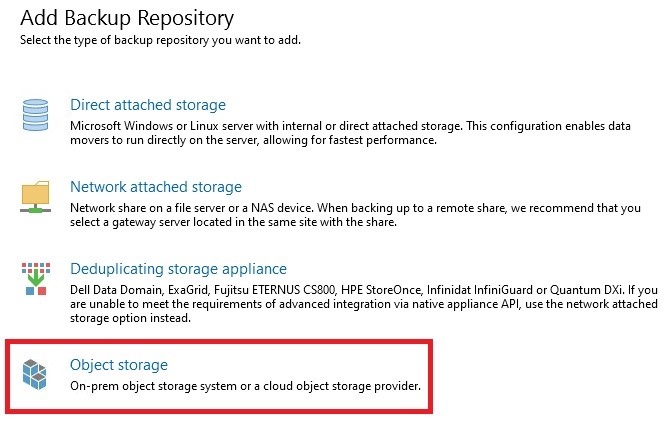
Now we can go to our Veeam B&R console, and from the main menu click on “Add Repository,” then select “Object Storage” and “Wasabi Cloud Storage”:
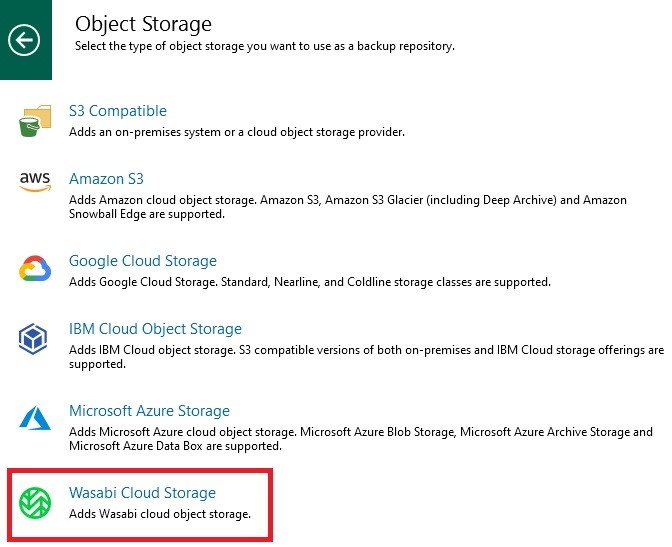
Once the wizard starts, enter the name we want to give on Veeam to our Wasabi repository:
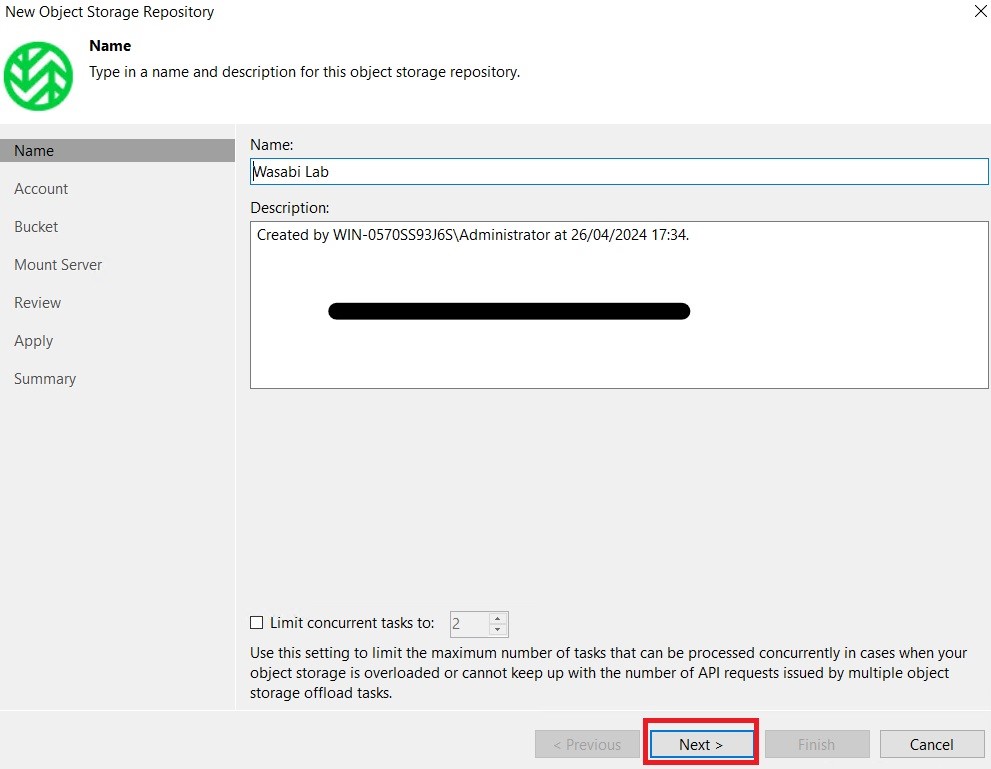
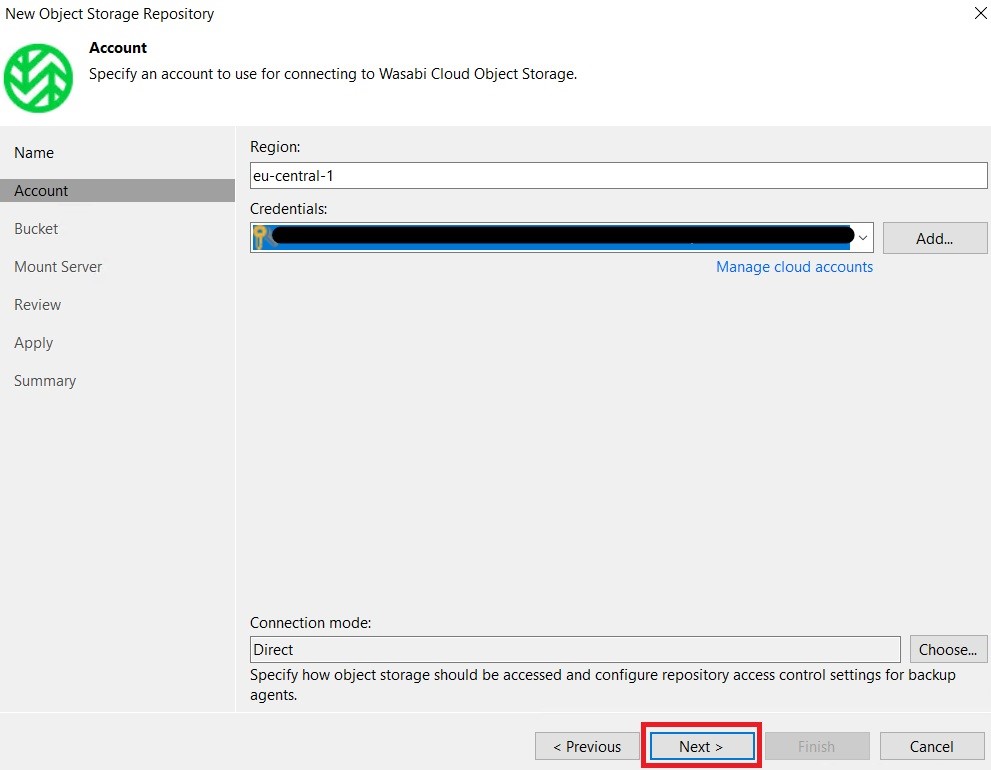
Next, enter the details of the storage account and region on which we created our bucket:
At this point, enter the details of the bucket and folder to be used for our backups:
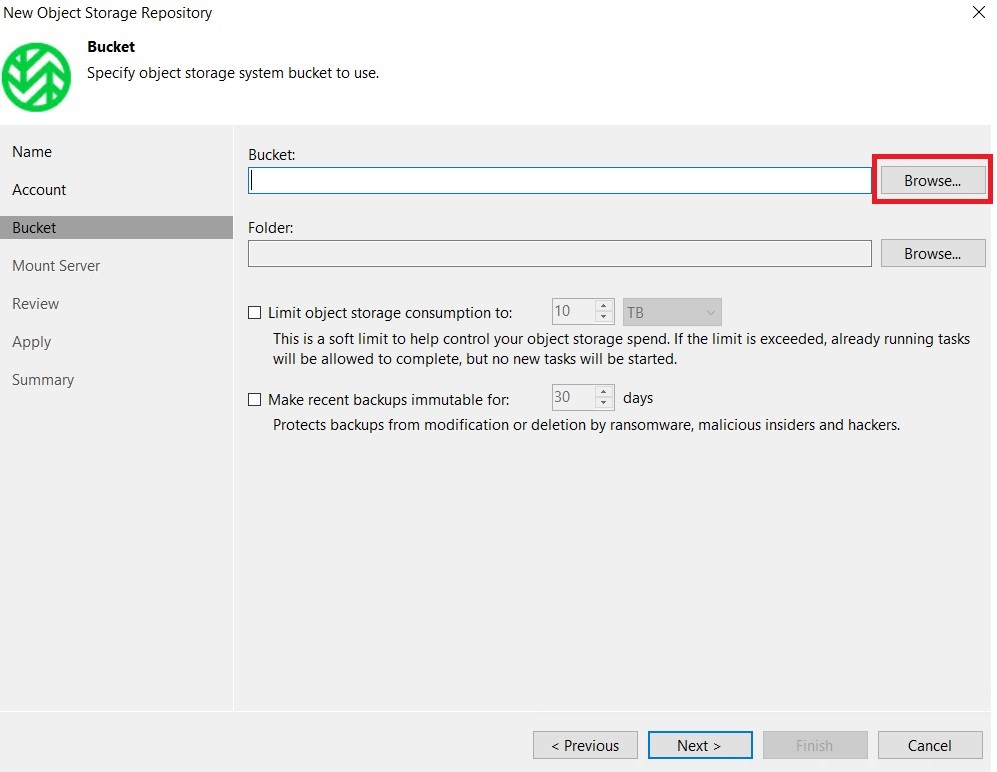
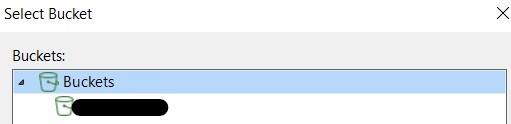
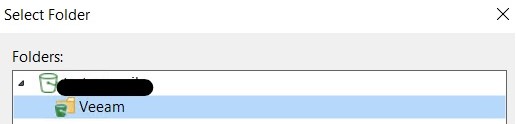
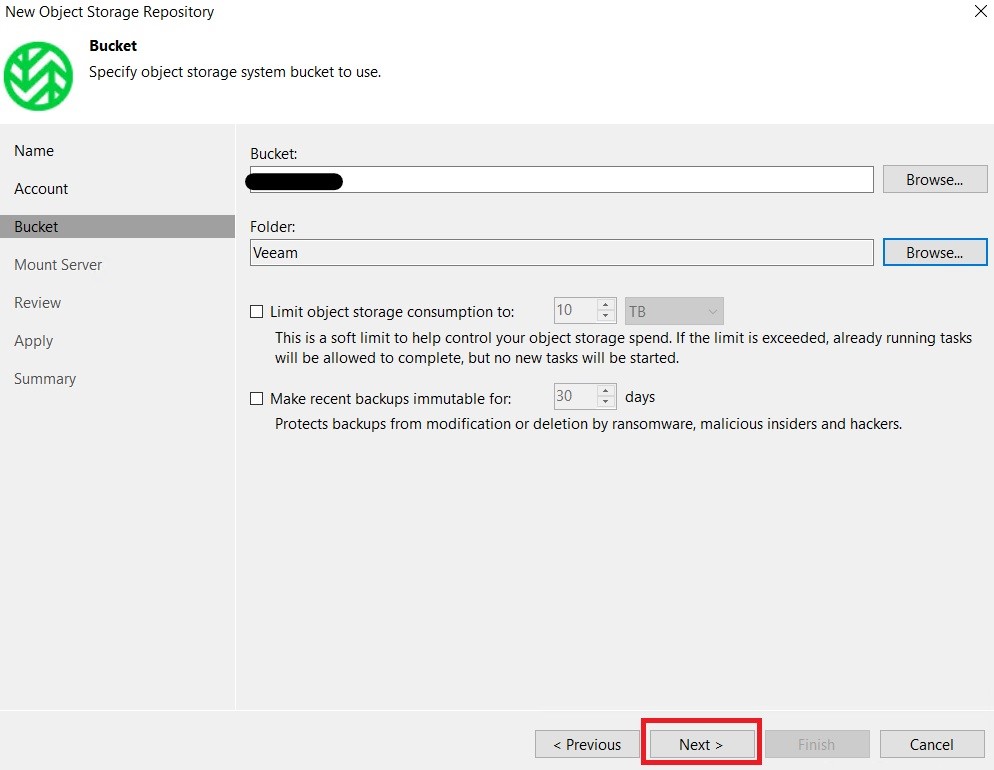
NB: for this tutorial in a lab environment the immutability flag was not enabled, but for production environments it is always recommended to use it
Finally, specify the mount server and complete the wizard:
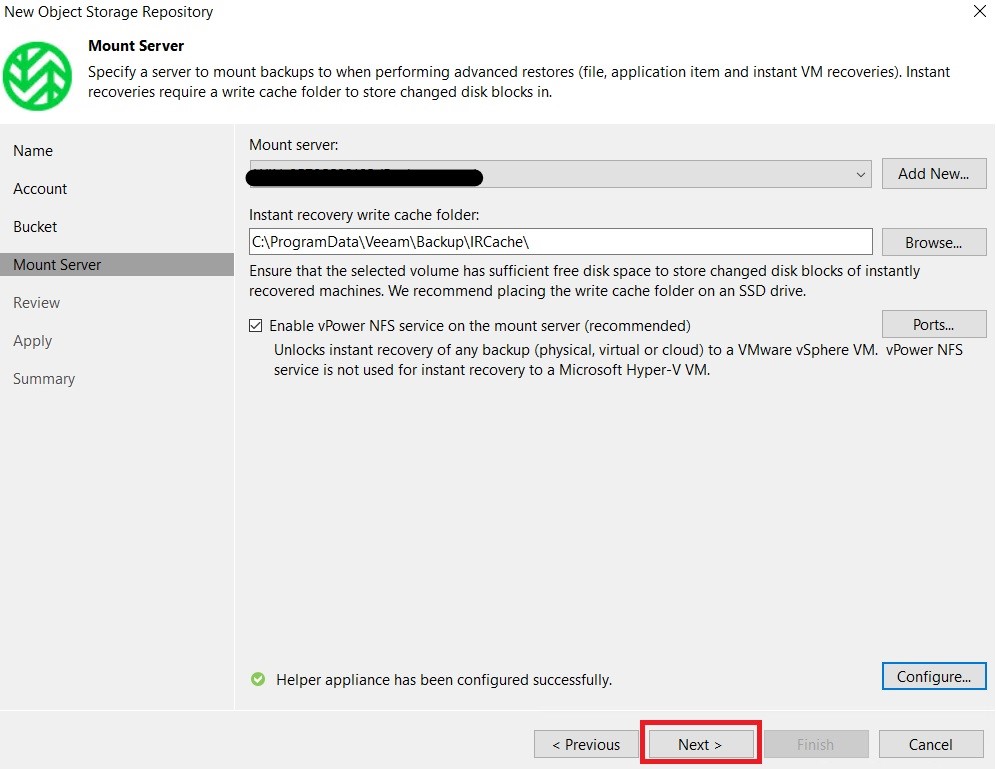
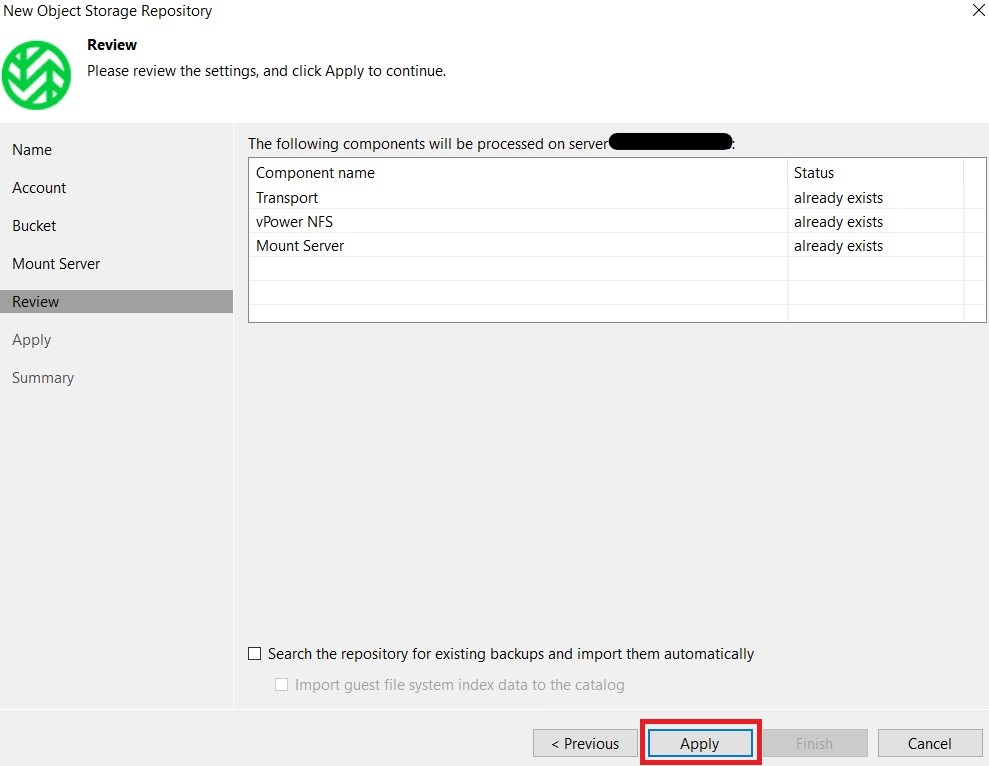
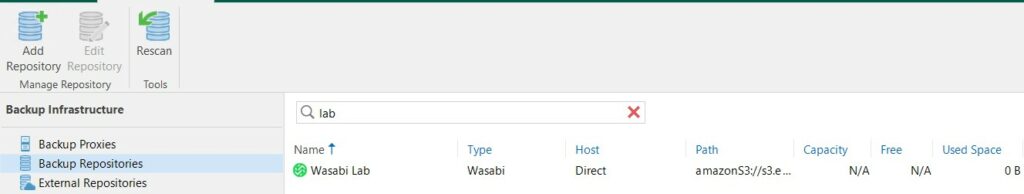
Here is our Wasabi repository to use for our backup jobs:
Enjoy! 💚